.png)
How to Access Geo-Restricted Content

Streaming platforms and research sites love to lock out content based on where you live. Over 50 percent of major websites now use advanced geo-restriction tools to block access for millions of people worldwide. Most assume these digital walls are just a minor annoyance and barely worth a second thought. But cracking the code to these hidden barriers is often the only way to unlock global information and even protect your privacy online.
Understanding Geo-Restrictions and Their Impact
Geo-restrictions represent a complex digital barrier that fundamentally limits online content access based on geographic location. These digital boundaries create significant challenges for users seeking unrestricted information, entertainment, and digital resources across global networks.
The Mechanics of Geographic Content Blocking
At its core, geo-restriction technology operates through sophisticated IP address tracking and verification systems. When you attempt to access online content, websites immediately analyze your IP address to determine your physical location. This process allows platforms to implement precise content filtering mechanisms that can block or alter content visibility depending on regional parameters.
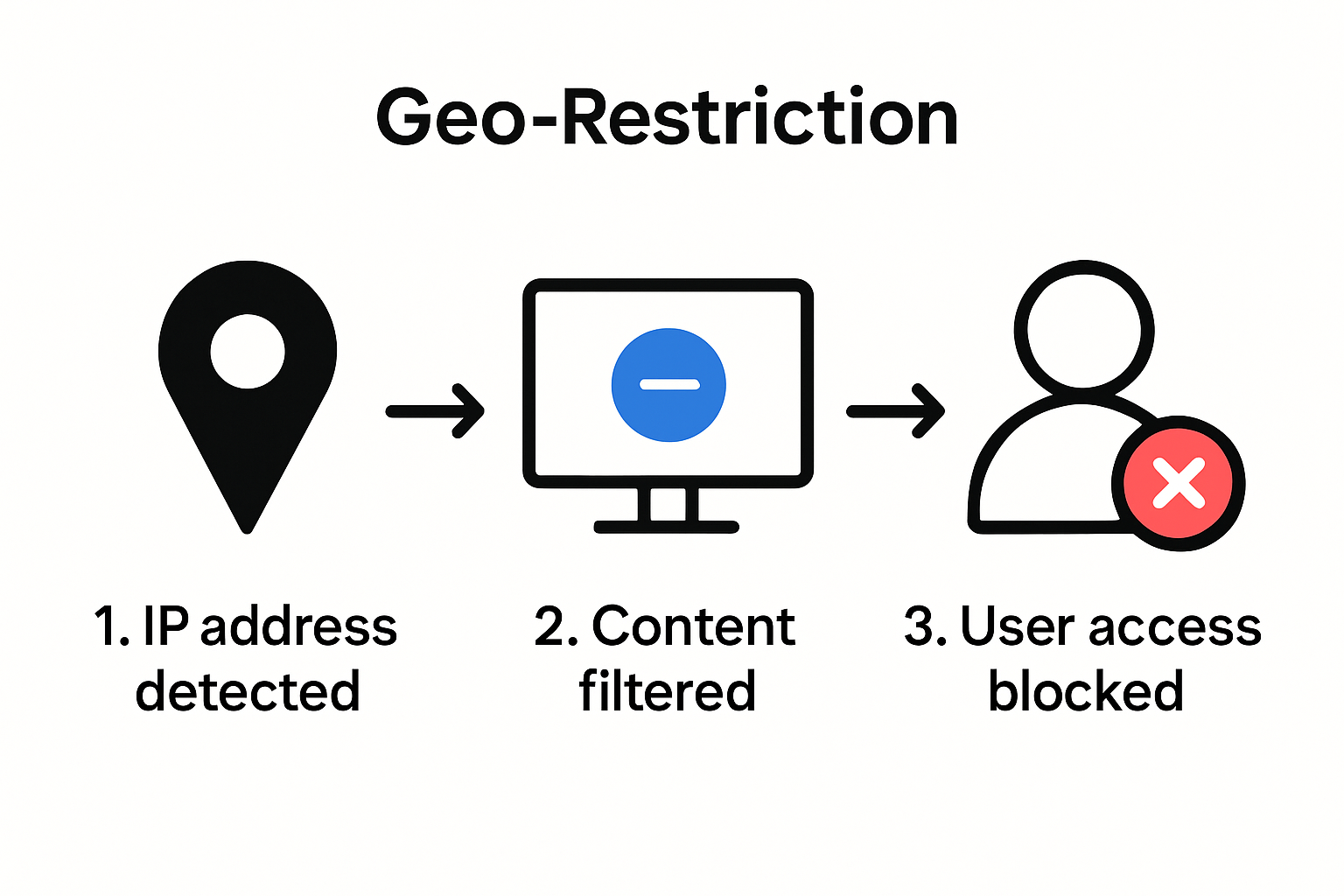
Research from the University of Michigan reveals that geoblocking practices are increasingly prevalent across multiple digital platforms. These restrictions can emerge from various motivations including licensing agreements, copyright regulations, economic pricing strategies, and regional content compliance requirements.
Global Impact and Technological Implications
The consequences of geo-restrictions extend far beyond simple content unavailability. Technological sovereignty becomes a critical issue as these digital barriers can significantly impede global knowledge exchange and collaborative opportunities. A comprehensive study in the Public Library of Science highlights the ethical implications of such restrictions, particularly in academic and research domains where information sharing is paramount.
Businesses, researchers, and individual users face substantial challenges when confronted with these digital boundaries. Academic researchers might be unable to access critical scientific publications, professionals could be restricted from utilizing global software platforms, and entertainment consumers frequently encounter frustrating roadblocks when attempting to stream content across international borders.
Understanding the Underlying Technology
Geo-restriction technologies leverage multiple sophisticated techniques to enforce regional content limitations. These include:
- IP Geolocation Tracking: Precise identification of user location through IP address analysis
- DNS Filtering: Blocking access based on domain name system configurations
- Server-Side Validation: Active verification of geographic origin during content request processes
Understanding these mechanisms provides crucial insight into how digital platforms implement and maintain geographic content controls. While designed to protect intellectual property and comply with regional regulations, these technologies simultaneously create significant barriers to open, unrestricted digital experiences.
Navigating these complex digital landscapes requires a nuanced approach that balances technological understanding with strategic access methodologies. As global digital ecosystems continue evolving, users must develop sophisticated strategies to overcome these geographic constraints effectively and ethically.
Best Tools to Access Geo-Restricted Content
Accessing geo-restricted content requires strategic technological solutions that can effectively bypass digital geographic barriers. While multiple tools exist, understanding their unique capabilities and potential limitations becomes crucial for users seeking unrestricted online experiences.
Virtual Private Networks (VPNs): The Primary Solution
Research analyzing VPN circumvention techniques demonstrates that Virtual Private Networks represent the most reliable method for accessing geo-restricted content. VPNs create encrypted tunnels that route internet traffic through servers located in different countries, effectively masking a user's actual geographic location.
The technical mechanism involves replacing your original IP address with an IP address from the VPN server's location. This process allows users to appear as though they are browsing from an entirely different geographic region, thus bypassing content restrictions seamlessly.
Smart DNS Services: Alternative Access Strategies
A comprehensive study on Smart DNS services reveals these technologies offer an alternative approach to circumventing geo-restrictions. Smart DNS services modify domain name system configurations, redirecting specific network traffic to bypass geographic blocking mechanisms without encrypting entire internet connections.
Key advantages of Smart DNS include faster connection speeds and less computational overhead compared to traditional VPN solutions. However, users should remain cautious about potential privacy vulnerabilities identified in the research. These services might expose user information more readily than fully encrypted VPN connections.
Legal and Technological Considerations
The Michigan Telecommunications & Technology Law Review highlights critical legal considerations surrounding geo-restriction circumvention. While technological tools exist, users must understand the potential legal implications of accessing content through alternative methods.
Users should consider several factors when selecting geo-restriction bypass tools:
- Connection Speed: Evaluate performance impact on internet browsing
- Privacy Protection: Assess encryption and data logging policies
- Server Locations: Verify availability of servers in desired regions
- Legal Compliance: Understand potential regulatory restrictions
Choosing the right tool requires balancing technological effectiveness with privacy considerations. Some services prioritize speed, while others focus on comprehensive security protocols. Experienced users often recommend utilizing multiple strategies or combining different tools to create robust access solutions.
As digital ecosystems continue evolving, geo-restriction bypass technologies will likewise advance. Staying informed about emerging techniques and understanding the intricate technological landscape becomes essential for users seeking unrestricted online experiences.
To help readers compare the main options for bypassing geo-restrictions, the following table summarizes key features and considerations of VPNs and Smart DNS services as discussed in this section.
Legal and Ethical Considerations for Professionals
Navigating geo-restriction bypass technologies requires a sophisticated understanding of complex legal and ethical frameworks. Professionals must carefully assess the potential implications of accessing restricted content beyond mere technological capabilities.
Ethical Frameworks and Content Access
Research from digital ethics scholars proposes critical principles for evaluating the ethical dimensions of content access. These principles recognize that geo-blocking is not inherently unethical but depends on specific contextual considerations such as intellectual property rights, regional licensing agreements, and content distribution mechanisms.
Professionals must critically examine their motivations for bypassing geo-restrictions. Legitimate research purposes, academic collaboration, and professional development might represent ethically defensible scenarios. Conversely, attempting to circumvent content restrictions purely for personal entertainment or financial gain could raise significant ethical concerns.
Professional Risk Assessment
A comprehensive study examining digital privacy behaviors reveals that many professionals underestimate the potential risks associated with geo-restriction circumvention. Understanding these risks becomes paramount for maintaining professional integrity and protecting organizational digital assets.
Key risk factors include:
- Compliance Violations: Potential breaches of institutional or corporate policies
- Legal Exposure: Risk of copyright infringement or contractual violations
- Data Security: Potential vulnerabilities introduced through unauthorized access methods
Institutional and Regulatory Considerations
Digital library research emphasizes the critical importance of maintaining data integrity and confidentiality. Professionals must align their content access strategies with established institutional guidelines and regulatory requirements.
Organizational leaders should develop clear protocols that:
- Define Acceptable Use: Establish transparent guidelines for content access
- Implement Monitoring: Create systems to track and validate access methods
- Provide Training: Educate professionals about legal and ethical implications
Effective navigation of geo-restriction challenges requires a holistic approach that balances technological capability with ethical responsibility. Professionals must develop nuanced strategies that respect intellectual property rights, maintain organizational integrity, and support legitimate professional objectives.
As digital ecosystems become increasingly complex, the ability to understand and ethically manage content access will become a critical professional competency. Continuous learning, strategic thinking, and a commitment to ethical principles will distinguish professionals who successfully operate within these evolving digital landscapes.
Optimizing Workflows with Access Solutions
Accessing geo-restricted content efficiently requires strategic workflow optimization that balances technological capabilities with professional productivity. Professionals must develop sophisticated approaches that minimize disruption while maximizing access to essential digital resources.
Intelligent Access Strategy Development
Research on secure content distribution reveals advanced techniques for optimizing access workflows. Professionals can implement intelligent strategies that prioritize authentication, minimize latency, and ensure consistent content availability across different geographic environments.
Effective workflow optimization involves creating comprehensive access protocols that anticipate potential technological barriers. This approach requires developing flexible systems that can quickly adapt to changing digital restrictions while maintaining robust security standards.
Network Traffic Management Techniques
Innovative network traffic obfuscation research demonstrates sophisticated methods for circumventing digital barriers without compromising overall network performance. Professionals can leverage these techniques to create more resilient and adaptive access solutions.
Key optimization strategies include:
- Dynamic IP Rotation: Implementing automated IP address switching to reduce detection risks
- Bandwidth Management: Allocating network resources strategically to maintain consistent access
- Multi-Platform Integration: Developing cross-platform access solutions that work seamlessly across different technological environments
Advanced Authentication and Access Control
Research on access control frameworks highlights the importance of developing sophisticated authentication mechanisms that balance security with accessibility. Professionals must design workflow solutions that provide granular control over content access while minimizing potential vulnerabilities.
Successful implementation requires a multifaceted approach that considers:
- Granular Permission Management: Creating precise access control mechanisms
- Real-Time Monitoring: Developing systems that track and validate access attempts
- Adaptive Authentication: Implementing intelligent verification processes that respond dynamically to potential security risks
The most effective access solutions transform technological limitations into strategic opportunities. By developing comprehensive workflows that anticipate and overcome digital barriers, professionals can create more resilient and flexible digital ecosystems.
As technological landscapes continue evolving, the ability to optimize access workflows will become increasingly critical. Professionals who can combine technical expertise with strategic thinking will be best positioned to navigate complex digital environments effectively and efficiently.


%20(76).png)
%20(75).png)
%20(74).png)
%20(73).png)
.png)
.png)
.png)
.png)
.png)
%20(72).png)
%20(70).png)
%20(68).png)
%20(66).png)
%20(64).png)
%20(63).png)
%20(62).png)
%20(60).png)
%20(59).png)
%20(58).png)
%20(57).png)
%20(52).png)
%20(51).png)
%20(49).png)
%20(48).png)
%20(46).png)
%20(45).png)
%20(44).png)
%20(43).png)
%20(42).png)
%20(41).png)
%20(40).png)
%20(37).png)
%20(36).png)
%20(35).png)
%20(33).png)
%20(32).png)
%20(30).png)
%20(29).png)
%20(27).png)
%20(26).png)
%20(25).png)
%20(24).png)
%20(22).png)
%20(21).png)
%20(20).png)
%20(19).png)
%20(18).png)
.svg)
%20(17).png)
%20(16).png)
%20(15).png)
%20(14).png)
%20(11).png)
%20(10).png)
%20(9).png)

%20(7).png)
%20(6).png)
%20(5).png)
%20(4).png)
%20(3).png)
%20(2).png)
.png)
.png)
%20(1).png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
